
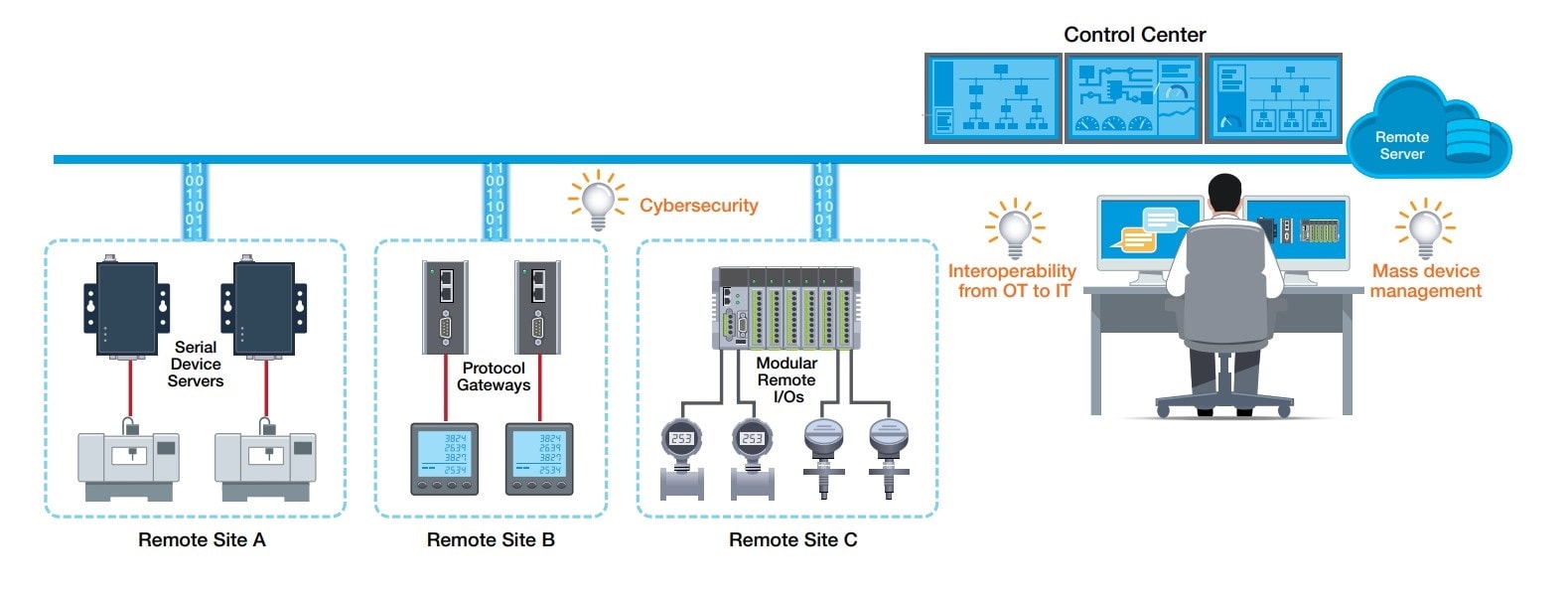
The IIoT has not only blurred the lines between OT and IT disciplines but also led to the increasing prevalence of large-scale and highly distributed applications where field devices are dispersed over a wide area and need to communicate directly with remote servers. This means that where your data is going to and from, how you manage all your different devices, and how you keep your data safe matter even more than before. In this section, we provide three additional tips you should keep in mind for selecting device connectivity solutions that can meet the demanding requirements of large-scale and highly distributed IoT applications in our connected world.
Key Question
With the widespread adoption of the IIoT, the traditional boundaries between OT and IT in industrial automation are becoming blurred. Are your devices ready to provide connectivity for large-scale and highly distributed applications in an increasingly interconnected world?
Stay on Top of Device Management
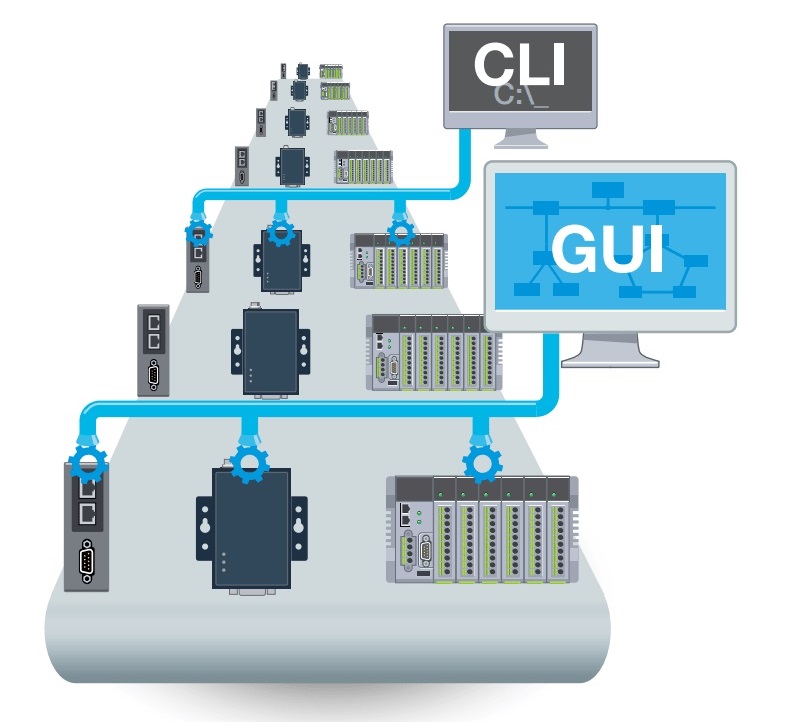
When you finally get all your field devices with multiple communication interfaces connected, another big question arises. How do you manage dozens or hundreds of different connectivity devices? During your daily operations, you need to monitor your connectivity devices to keep them up-to-date with the latest firmware and minimize unauthorized access and potential intrusions by updating device login credentials for every user. Such tasks might not be an issue when there are only a few devices and one type of connectivity device. However, it can be a tremendous burden if dozens of different connectivity devices are used in your IIoT application.
Having a software tool or utility that can help you manage large amounts of different connectivity devices can make daily operations much easier. With the lines between the IT and OT worlds becoming increasingly blurry in the IIoT era, management tools need to be flexible enough to serve users in both domains. Besides mass device management capabilities, the connectivity device you choose should have both a GUI for OT users and a CLI for IT users to optimize IIoT system maintenance.
As Always, Cybersecurity Matters
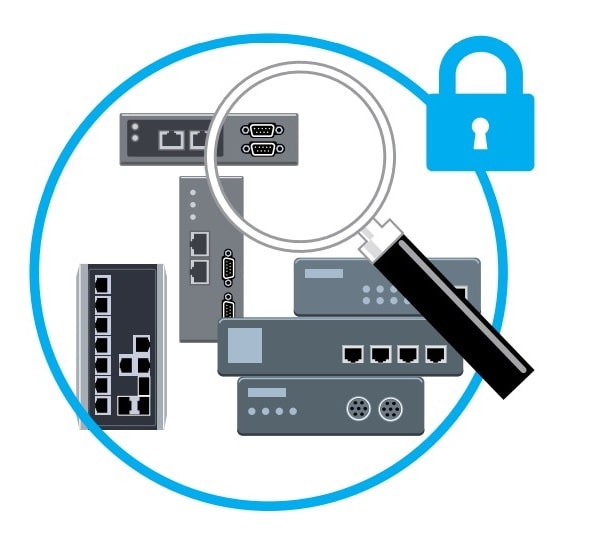
This isn’t the first time we’ve mentioned cybersecurity—and it won’t be the last! The truth is, that the diversity of end devices in industrial field sites, distributed architectures, and legacy systems increases the security risk of your IIoT applications because most of these devices are not designed with cybersecurity in mind. As a result, it is essential to select connectivity solutions with built-in security features and place them in front of your end devices. But with so many connectivity solutions on the market to fulfill the communication demands of different edge devices, how can you ensure your field data are well protected? Enter the IEC 62443 standard, a set of global security guidelines that list specific security requirements for device manufacturers to ensure the device you choose meets the latest cybersecurity standards.
When selecting a connectivity device, refer to the following checklist to ensure that the vendor has sufficient security expertise and provides relevant services and that the device comes with future-proof security designs.
Vendor Selection
- Select vendors that are certified for secure product development
- Select vendors that provide security documents, such as hardening guides and questionnaires, as well as security services like pre-sales consultancy, post-sale vulnerability scanning, and security patching.
Product Selection
- Select products with a secure boot to ensure the device will only operate trusted firmware/image provided by the original vendor.
- Select products with authenticity and integrity checks to validate that the uploaded firmware/configuration can not be tampered with.
- Select products with role-based access control (RBAC) to identify and grant the least privilege to different user groups to control who and what they can do on the devices.
- Select products with device-level network IP filtering to prevent
unwarranted connections.
- Select products with serial data encryption on Ethernet to protect the integrity of sensitive data.
- Select products with the capability to be monitored on the security operation center (SoC) or network management system (NMS) for asset visibility and change monitor for future maintenance.
Related Products
- MOXA Serial Device Servers >Go to the product page
- MOXA Protocol Gateways >Go to the product page
- MOXA Modular Remote I/Os >Go to the product page
Expert Advice
Enabling device connectivity for large-scale or highly distributed IIoT applications in an increasingly the connected world requires a smooth communications between OT and IT systems, powerful device manageability, and uncompromised cybersecurity.
*For any further information please contact us via info@rockford-qatar.com.





-150x150.png)


