In the realm of remote device access,
safeguarding security is paramount. Fundamental practices like altering default
passwords, fortifying ports, and deactivating superfluous services are
essential for local device security. However, the system must also contend with
external threats that could disrupt data flow or, in dire circumstances,
jeopardize its integrity.
Remote
communication offers various avenues, spanning public and private
infrastructure, with encryption serving as a linchpin for both. One strategy to
shield against external perils involves crafting a private infrastructure
through cellular or fixed-line technology. Essentially, this network functions
akin to the internet, yet remains exclusive to designated users. This
facilitates interconnectivity between high-tier systems and remote devices,
bolstering privacy. Nevertheless, it's worth noting that the information
transmitted within this framework lacks encryption or security.
The
internet, despite its ubiquity, poses its own security challenges when deployed
for remote communication. Notably, transmission between top-tier hubs and
remote sites may lack privacy. Skillful individuals can intercept and monitor
traffic without much difficulty. This underscores the criticality of employing
encryption and a virtual private network (VPN) to ensure data protection.
Choosing
between public and private networks hinges on various factors. Public networks,
exemplified by the internet, facilitate billions of secure communications
across sites. Private networks, while pricier due to their privacy benefits,
may not necessarily offer encryption. This is where VPNs and protocols like
Secure Socket Layer (SSL) come into play, reinforcing communication security.
SSL leverages certificates to establish trust between entities, utilizing
shared public keys and concealed private keys. Routine validation ensures the
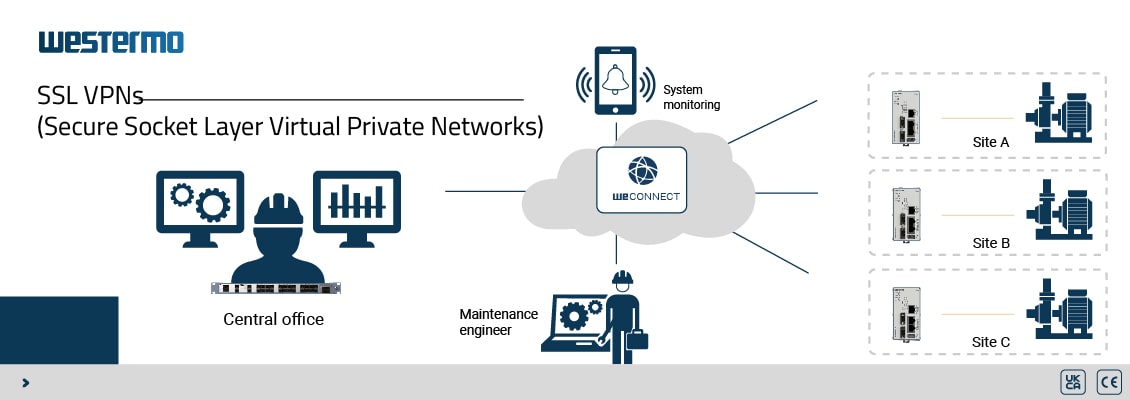
keys' legitimacy within the network infrastructure. Notably, WeConnect is an
exemplar of SSL encryption extensively employed in mission-critical sectors such
as Oil and gas, Shipping, Power, Water and wastewater, and Aviation.
Effective
certificate management necessitates a trusted authority. One of SSL's standout
advantages is its capacity to distribute and revoke certificates. Regular
updates ensure network security and seamless communication. The suspicious
activity prompts authorities to invalidate and reissue certificates, thereby
sustaining operational continuity between Site A and Site B, even over public
networks.
Irrespective of your chosen methodology, the Merlin range stands ready. For both public and private infrastructures, SSL VPNs fortified with cellular connectivity empower remote outstations with an added layer of protection.
Featured Product

Industrial Cellular Router
Merlin-4407-T4-S2-LV
The robust and compact Merlin 4400 cellular router is the ideal fit for utility and industrial applications. It features zero-touch large-scale deployment and comprehensive cybersecurity capabilities, such as secure boot and TPM (Trusted Platform Module).
*For any further information please contact us via info@rockford-qatar.com.





-150x150.png)


